The code is vulnerable to? Can you answer this? #hacker #cybersecurity #coding #computer #shorts
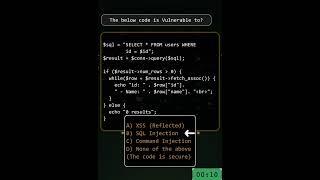
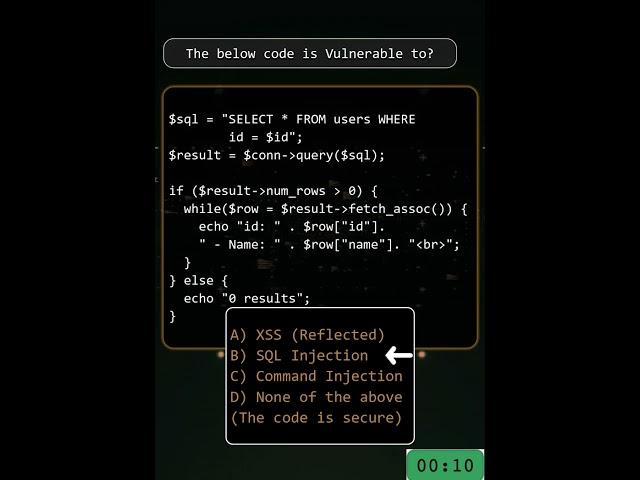
The below code is vulnerable to which vulnerability?
A. XSS - Cross Site Scripting
B. SQL Injection
C. Command Injection
D. None of the above (the code is secure)
#ethicalhacking #hacking #hacker #programming #cybersecurity #coding #javascript #ethicalhacker #language #computerscience #computer #html #css #csstricks #javascript #hacker #htmltutorial #websecurity #xss #htmlinjection #sql
A. XSS - Cross Site Scripting
B. SQL Injection
C. Command Injection
D. None of the above (the code is secure)
#ethicalhacking #hacking #hacker #programming #cybersecurity #coding #javascript #ethicalhacker #language #computerscience #computer #html #css #csstricks #javascript #hacker #htmltutorial #websecurity #xss #htmlinjection #sql
Тэги:
#ethical_hacking ##ethical_hacking ##ethical_#hacking ##ethical ##hacking ##ethical_hacking_programming #programming #languages ##programming ##languages ##programming_languages_for_ethical_hacking ##python_for_hacking ##cpp_for_hacking ##javascript_for_hacking ##ruby_for_hacking ##programming_for_hacking ##sql_for_hacking ##cyber_security ##ethical_hackers ##top5 ##top10 #top_5_languages ##python #Python ##pythontips #turtle #library #html ##html ##javascript #css #HTML ##websecurity #websecurity #sqlКомментарии:

@prodigiousMind - 20.01.2024 17:28
The code is vulnerable to SQL Injection due to the lack of validation of the user controlled parameter (i.e. $id).
So, the correct option is B) SQL Injection
PoC: id=-1337 OR '1'='1';# --
The above will return back results for all ids due to '1'='1' as always being TRUE.
Prevention:
It’s important to always sanitize and validate user inputs to prevent such vulnerabilities. For PHP, we can use prepared statements with parameter binding to prevent SQL Injection.

@EvictoMonteiro - 22.01.2024 23:24
B
Ответить
Введение | ФИЛОСОФИЯ ЗА 5 МИНУТ
Дима Богомолов
Евгений Понасенков гуляет,но это майнкрафт
идеальный градиент
Про болевые ощущения. Это больно?
Smas Lifting
It's Tricky - GTA San Andreas Music Video
Go sub to Gold Productions (link in about tab)
1989 Euro-America Cup
kevmcg
Winter fishing for bream, fish! Raises a nod at night in the tent
РЫБАФАН на рыбалке
68)Senjojiki curl to Mt.Kisokomagatake(Japan's most iconic alpine scenery)
Castle tour of Japan channel