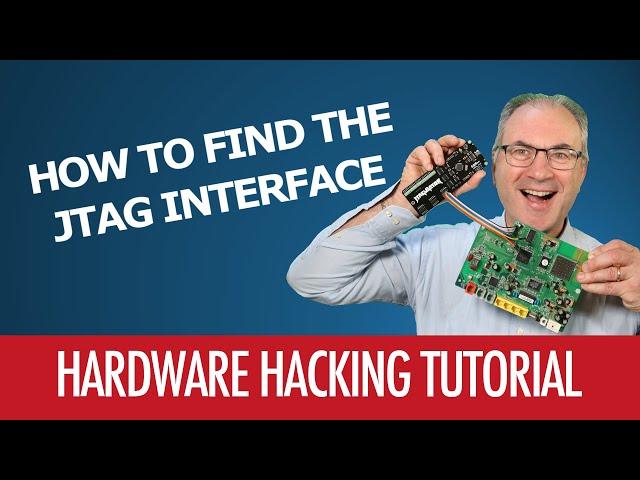
#03 - How To Find The JTAG Interface - Hardware Hacking Tutorial
In this video I will introduce the JTAG interface, an interface that you can find on almost all of your IoT devices like routers, webcams, electronic toys, TV remotes and so on.
I will explain why this interface can be so useful in hardware hacking and how to find its position and pin-out using simple techniques like, for example, using a multi-meter or a cheap Jtagulator board. And when the pin-out is known, but the JTAG interface is not working, I will explain the reasons why this can happen and what to do to solve the issue.
*** What is the JTAG interface
JTAG is an industry standard, usually implemented in complex integrated circuits; this standard was issued for the first time in 1990, with the purpose to simplify the testing of PCB after manufacture.
It allowed controllability and observability of each bit of internal memory of each integrated circuit and allowed to check the integrity of each single trace connecting different integrated circuits in the PCB.
It allows reading and writing the flash memory content and, with later improvement to the standard, it can be used as a mean to do in-circuit debugging that means being able to run a debugger on the real firmware running on the real hardware.
*** Why JTAG interface is important in Hardware Hacking
- it allows to read and write the content of the EEPROM, so it can be used to dump the entire EEPROM content. It can also be used to restore the original firmware in case of bricking the device during our firmware modification trials.
- it allows to break into the boot cycle and use the JTAG interface as a mean to do "in circuit debugging" this means using a debugger with the real firmware on the real hardware
*** How to find the JTAG interface
To find the position of the JTAG interface we follow "the easiest path first" principle, this means that first of all we search on Internet to see if someone else has already done the job for us and has already found where is located the JTAG interface in our device.
We can start looking at the board searching for pins labeled with the names of the JTAG interface like TCK, TDI, TDO and TMS.
If we are not lucky in searching on Internet or in looking at labels on our board, finding the position of the JTAG interface it's not easy; one of the reasons is that there are no standardised connectors and pin-out; anyway there are few popular pin-outs, some of these pin-outs are available on the jtagtest website, link below.
If we don't find any JTAG pin label on our board, we start searching for pin headers arranged in a single row of 5 or 6 pins or in a double row of 10, 12, 14, or 20 pins.
When we have found the pin candidates we can use a multi-meter to find the possible pin-out because finding GND and VCC is easy, usually TMS and TDI have a pull-up resistor, TRST usually can have a pull up or a pull down resistor and TDO should be an high impedance input.
Once we have identified GND, VCC and taken pin resistance and voltage measurements we can compare what we have found with popular pin-out in the jtagtest website and, if we are lucky, we can identify the JTAG pinout using a simple multi-meter.
If we know the System On a Chip and if we have his data sheet we can locate the JTAG pins on the chip and then follow PCB traces to identify the connector, but this is usually very difficult for two possible reasons:
- often the System On a Chip is a SMD with pins below the package and it is impossible to identify them on the Printed Circuit Board
- when the System On a Chip has a package that shows his pin and is easy to identify the JTAG pins, it can be difficult to follow the traces on a multi-layer board and today, almost all boards are multi-layer.
The best and easy solution, once we have identified potential JTAG pin candidates, is to use Jtagulator, it has a lot of headers that we can attach to potential JTAG pin candidates, it can run some automatic scanning logic and identify the JTAG pinout.
-------------------------------
Links with additional Information
Channel’s Author: https://www.makemehack.com/2020/02/a-short-introduction-of-myself.html
Channel’s Web Site: https://www.makemehack.com/
The sample router (Gemtek WVRTM-127ACN) on techinfodepot: http://en.techinfodepot.shoutwiki.com/wiki/Gemtek_WVRTM-127ACN
The sample router (Gemtek WVRTM-127ACN) reverse engineered on GitHub: https://github.com/digiampietro/hacking-gemtek
The JTagulator website: http://www.grandideastudio.com/jtagulator/
TTL Serial Adapter (affiliate link): https://amzn.to/2vvzCYB
PuTTY, the terminal emulator: https://www.putty.org/
Bus Pirate: http://dangerousprototypes.com/docs/Bus_Pirate
Bus Bluster: http://dangerousprototypes.com/docs/Bus_Blaster
J-Link Debug Probes: https://www.segger.com/products/debug-probes/j-link/
OpenOCD: http://openocd.org/
Website with popular JTAG pinout: http://www.jtagtest.com/pinouts/
Previous episode #02: https://youtu.be/6_Q663YkyXE
I will explain why this interface can be so useful in hardware hacking and how to find its position and pin-out using simple techniques like, for example, using a multi-meter or a cheap Jtagulator board. And when the pin-out is known, but the JTAG interface is not working, I will explain the reasons why this can happen and what to do to solve the issue.
*** What is the JTAG interface
JTAG is an industry standard, usually implemented in complex integrated circuits; this standard was issued for the first time in 1990, with the purpose to simplify the testing of PCB after manufacture.
It allowed controllability and observability of each bit of internal memory of each integrated circuit and allowed to check the integrity of each single trace connecting different integrated circuits in the PCB.
It allows reading and writing the flash memory content and, with later improvement to the standard, it can be used as a mean to do in-circuit debugging that means being able to run a debugger on the real firmware running on the real hardware.
*** Why JTAG interface is important in Hardware Hacking
- it allows to read and write the content of the EEPROM, so it can be used to dump the entire EEPROM content. It can also be used to restore the original firmware in case of bricking the device during our firmware modification trials.
- it allows to break into the boot cycle and use the JTAG interface as a mean to do "in circuit debugging" this means using a debugger with the real firmware on the real hardware
*** How to find the JTAG interface
To find the position of the JTAG interface we follow "the easiest path first" principle, this means that first of all we search on Internet to see if someone else has already done the job for us and has already found where is located the JTAG interface in our device.
We can start looking at the board searching for pins labeled with the names of the JTAG interface like TCK, TDI, TDO and TMS.
If we are not lucky in searching on Internet or in looking at labels on our board, finding the position of the JTAG interface it's not easy; one of the reasons is that there are no standardised connectors and pin-out; anyway there are few popular pin-outs, some of these pin-outs are available on the jtagtest website, link below.
If we don't find any JTAG pin label on our board, we start searching for pin headers arranged in a single row of 5 or 6 pins or in a double row of 10, 12, 14, or 20 pins.
When we have found the pin candidates we can use a multi-meter to find the possible pin-out because finding GND and VCC is easy, usually TMS and TDI have a pull-up resistor, TRST usually can have a pull up or a pull down resistor and TDO should be an high impedance input.
Once we have identified GND, VCC and taken pin resistance and voltage measurements we can compare what we have found with popular pin-out in the jtagtest website and, if we are lucky, we can identify the JTAG pinout using a simple multi-meter.
If we know the System On a Chip and if we have his data sheet we can locate the JTAG pins on the chip and then follow PCB traces to identify the connector, but this is usually very difficult for two possible reasons:
- often the System On a Chip is a SMD with pins below the package and it is impossible to identify them on the Printed Circuit Board
- when the System On a Chip has a package that shows his pin and is easy to identify the JTAG pins, it can be difficult to follow the traces on a multi-layer board and today, almost all boards are multi-layer.
The best and easy solution, once we have identified potential JTAG pin candidates, is to use Jtagulator, it has a lot of headers that we can attach to potential JTAG pin candidates, it can run some automatic scanning logic and identify the JTAG pinout.
-------------------------------
Links with additional Information
Channel’s Author: https://www.makemehack.com/2020/02/a-short-introduction-of-myself.html
Channel’s Web Site: https://www.makemehack.com/
The sample router (Gemtek WVRTM-127ACN) on techinfodepot: http://en.techinfodepot.shoutwiki.com/wiki/Gemtek_WVRTM-127ACN
The sample router (Gemtek WVRTM-127ACN) reverse engineered on GitHub: https://github.com/digiampietro/hacking-gemtek
The JTagulator website: http://www.grandideastudio.com/jtagulator/
TTL Serial Adapter (affiliate link): https://amzn.to/2vvzCYB
PuTTY, the terminal emulator: https://www.putty.org/
Bus Pirate: http://dangerousprototypes.com/docs/Bus_Pirate
Bus Bluster: http://dangerousprototypes.com/docs/Bus_Blaster
J-Link Debug Probes: https://www.segger.com/products/debug-probes/j-link/
OpenOCD: http://openocd.org/
Website with popular JTAG pinout: http://www.jtagtest.com/pinouts/
Previous episode #02: https://youtu.be/6_Q663YkyXE
Тэги:
#Locating_JTAG #Identifying_JTAG #How_to_find_JTAG #Finding_JTAG #JTAG_Hacking #Find_JTAG #Find_JTAG_pins #Find_JTAG_pinout #JTAG #IoT_JTAG #How_to_use_Jtagulator #Jtagulator #JTAG_not_working #Hardware_Hacking_Tutorial #Hardware_Hacking #How_To_Do_Hardware_Hacking #Practical_Hardware_Hacking #Hardware_Hacking_for_beginners #Reverse_Engineering #Reverse_Engineering_Hardware_Tutorial #Practical_Hacking #Hacking_Tutorial #Hacking_for_beginners #Router_HackingКомментарии:
Сигареты с гималайским табаком - ESSE Himalay
Макс Фрунзе
Саунаға апарып аямай сікті ️
Ам жалау
How Long Gone
Brooks & Dunn
музыка релакс добрая
SanyaKilLo
Tier-1 competitive Scrims Highlights | Team SouL
SOUL Regaltos
TRINITY GTA В 2013 ГОДУ! Каким был Trinity раньше?
drakosiemens
"Когда я на почте cлужил ямщиком", переложение Елютина
alexander maev