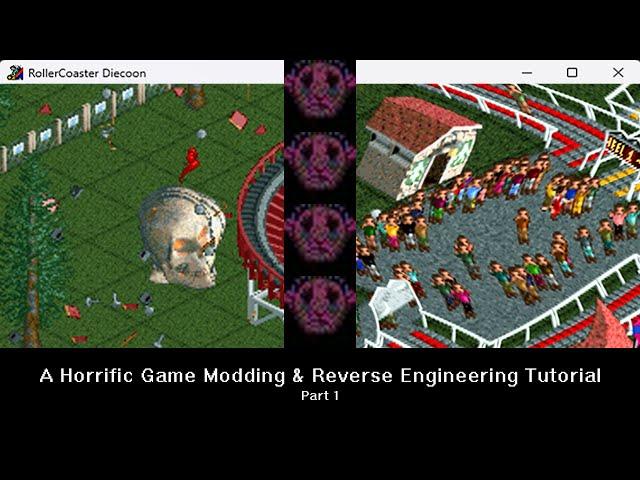
Modding RollerCoaster Tycoon into a Peele Horror Film (Game Modding/Reverse Engineering Tutorial)
This tutorial showcases how to write a RollerCoaster Tycoon mod in Python that implements the following "horrific" changes to the gameplay:
Any roller coaster crash/explosion will trigger the following:
1. A spinning skull animation at the crash site (animation can be changed)
2. A horror soundtrack which plays in the background (track can be changed)
3. Guests in the park will turn towards the player and applaud
Plus, the game window title will be renamed to "RollerCoaster Diecoon"...because "horror"...
This is Part 1/2 of the tutorial: Part 1 covers the reversing of RCT's graphics/sound systems and the building of the horror mod, while Part 2 deep dives into the Python and shellcode used to automate this mod (linked in the repo below).
After months of research, reversing, and coding, I am beyond happy to finally share this one with you all - Thanks, truly, for the patience and support as without it, this video may have never been finished.
But now I'm so happy to have stuck with it, and I hope you enjoy this journey of bringing a stupid, silly fever dream to light, while learning a ton about game hacking/modding and reversing.
Please leave feedback and questions here as comments, or DM me on Mastodon (social links listed on the channel).
Check the pinned comment for any updates to the content.
Let me know what you would like to see in future videos!
Project Homepage:
https://github.com/jeFF0Falltrades/Tutorials/tree/master/rct_horror_mod
Resources and References:
Tooling:
Ghidra: https://ghidra-sre.org/
IDA: https://hex-rays.com/ida-free/
x64dbg: https://x64dbg.com/
Online Assembler/Disassembler: https://defuse.ca/online-x86-assembler.htm#disassembly
Python dataclass Docs: https://docs.python.org/3/library/dataclasses.html
RCT Technical Information Depot and More:
https://tid.rctspace.com/
https://rv.rctspace.com/?rv=hwinkels2
https://strategywiki.org/wiki/RollerCoaster_Tycoon/Walkthrough
Windows Library/Graphics Resources:
https://www.tech-insider.org/windows/research/acrobat/940929-a.pdf
https://github.com/Subhankar2000/DOS_BOX/tree/3fd3ede104b3ea35761b4df20d6af424c6627087/WINDOWS_3.1/C/WING/SAMPLES
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/nf-wingdi-stretchdibits
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-bitmapinfo
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-bitmapinfoheader
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-rgbquad
https://learn.microsoft.com/en-us/windows/win32/gdi/device-independent-bitmaps
https://en.wikipedia.org/wiki/BMP_file_format
https://en.wikipedia.org/wiki/Microsoft_Windows_library_files
https://learn.microsoft.com/en-us/previous-versions/dd757161(v=vs.85)
https://www-user.tu-chemnitz.de/~heha/petzold/ch15c.htm
https://www-user.tu-chemnitz.de/~heha/petzold/petzold.htm
https://www.compuphase.com/palette.htm
GTA footage provided by @NoCopyrightGameplays - Thank you!
Chapters in Part 1:
00:00:00 - Intro
00:03:18 - Important Notes
00:04:52 - Welcome/Brief note of appreciation
00:07:02 - Setup and initial analysis
00:18:01 - GDI32.DLL and StretchDIBits()
00:30:13 - Device-Independent Bitmaps
00:36:20 - BITMAPINFO(HEADER) structs and the color table
00:39:04 - ChatGPT lets us all down
00:50:28 - Extracting DIB and palette data from the RCT process
00:54:19 - Dynamically calculating the DIB & color palette locations
01:07:00 - Q: How is graphics data loaded into the DIB?
01:14:16 - A: CSG1.dat contains the RCT graphics data
01:17:41 - Q: How does the game decide which data to load from CSG1.dat?
01:27:37 - A: Discovering CSG1i.dat
01:33:25 - RCT TID, James Hughes, and Henry Winkelstein save the day
01:38:30 - CSG1i.dat's relationship to CSG1.dat
01:46:25 - Extracting bitmaps from CSG1.dat
01:50:00 - Finding the explosion and applause bitmaps
01:53:11 - Finding where the explosion is triggered in the game logic
01:59:19 - Replacing the explosion with something else
02:04:33 - Triggering the applause animation
02:16:54 - Adding a spooky soundtrack
02:18:24 - Sounds, mciSendStr(), and CSS.DAT files
02:23:28 - Glueing the mod together
02:25:47 - Writing the mod shellcode
02:30:41 - Bringing the vision to life
02:33:04 - Congratulations and stay tuned for pt. 2
Any roller coaster crash/explosion will trigger the following:
1. A spinning skull animation at the crash site (animation can be changed)
2. A horror soundtrack which plays in the background (track can be changed)
3. Guests in the park will turn towards the player and applaud
Plus, the game window title will be renamed to "RollerCoaster Diecoon"...because "horror"...
This is Part 1/2 of the tutorial: Part 1 covers the reversing of RCT's graphics/sound systems and the building of the horror mod, while Part 2 deep dives into the Python and shellcode used to automate this mod (linked in the repo below).
After months of research, reversing, and coding, I am beyond happy to finally share this one with you all - Thanks, truly, for the patience and support as without it, this video may have never been finished.
But now I'm so happy to have stuck with it, and I hope you enjoy this journey of bringing a stupid, silly fever dream to light, while learning a ton about game hacking/modding and reversing.
Please leave feedback and questions here as comments, or DM me on Mastodon (social links listed on the channel).
Check the pinned comment for any updates to the content.
Let me know what you would like to see in future videos!
Project Homepage:
https://github.com/jeFF0Falltrades/Tutorials/tree/master/rct_horror_mod
Resources and References:
Tooling:
Ghidra: https://ghidra-sre.org/
IDA: https://hex-rays.com/ida-free/
x64dbg: https://x64dbg.com/
Online Assembler/Disassembler: https://defuse.ca/online-x86-assembler.htm#disassembly
Python dataclass Docs: https://docs.python.org/3/library/dataclasses.html
RCT Technical Information Depot and More:
https://tid.rctspace.com/
https://rv.rctspace.com/?rv=hwinkels2
https://strategywiki.org/wiki/RollerCoaster_Tycoon/Walkthrough
Windows Library/Graphics Resources:
https://www.tech-insider.org/windows/research/acrobat/940929-a.pdf
https://github.com/Subhankar2000/DOS_BOX/tree/3fd3ede104b3ea35761b4df20d6af424c6627087/WINDOWS_3.1/C/WING/SAMPLES
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/nf-wingdi-stretchdibits
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-bitmapinfo
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-bitmapinfoheader
https://learn.microsoft.com/en-us/windows/win32/api/wingdi/ns-wingdi-rgbquad
https://learn.microsoft.com/en-us/windows/win32/gdi/device-independent-bitmaps
https://en.wikipedia.org/wiki/BMP_file_format
https://en.wikipedia.org/wiki/Microsoft_Windows_library_files
https://learn.microsoft.com/en-us/previous-versions/dd757161(v=vs.85)
https://www-user.tu-chemnitz.de/~heha/petzold/ch15c.htm
https://www-user.tu-chemnitz.de/~heha/petzold/petzold.htm
https://www.compuphase.com/palette.htm
GTA footage provided by @NoCopyrightGameplays - Thank you!
Chapters in Part 1:
00:00:00 - Intro
00:03:18 - Important Notes
00:04:52 - Welcome/Brief note of appreciation
00:07:02 - Setup and initial analysis
00:18:01 - GDI32.DLL and StretchDIBits()
00:30:13 - Device-Independent Bitmaps
00:36:20 - BITMAPINFO(HEADER) structs and the color table
00:39:04 - ChatGPT lets us all down
00:50:28 - Extracting DIB and palette data from the RCT process
00:54:19 - Dynamically calculating the DIB & color palette locations
01:07:00 - Q: How is graphics data loaded into the DIB?
01:14:16 - A: CSG1.dat contains the RCT graphics data
01:17:41 - Q: How does the game decide which data to load from CSG1.dat?
01:27:37 - A: Discovering CSG1i.dat
01:33:25 - RCT TID, James Hughes, and Henry Winkelstein save the day
01:38:30 - CSG1i.dat's relationship to CSG1.dat
01:46:25 - Extracting bitmaps from CSG1.dat
01:50:00 - Finding the explosion and applause bitmaps
01:53:11 - Finding where the explosion is triggered in the game logic
01:59:19 - Replacing the explosion with something else
02:04:33 - Triggering the applause animation
02:16:54 - Adding a spooky soundtrack
02:18:24 - Sounds, mciSendStr(), and CSS.DAT files
02:23:28 - Glueing the mod together
02:25:47 - Writing the mod shellcode
02:30:41 - Bringing the vision to life
02:33:04 - Congratulations and stay tuned for pt. 2
Тэги:
#assembly #beginner #c_programming #computer #computer_architecture #computer_programming #computer_science #cyber #cybersecurity #debugging #education #free_online_course #game_hacking #game_modding #game_patching #gaming #ghidra #github #hacking #henry_winkelstein #information_security #intermediate #james_hughes #malware #malware_analysis #modding #patching #programming #python #reverse #reverse_engineering #rollercoaster_tycoon #security #technology #tutorial #video_games #x64dbgКомментарии:
#ягдтерьер #Наша охрана)) #ягдтерьер #мокрыйнос #собакен #друг #охота #любовь #shorts
Обо всём на позитиве)
Nightcore - Circus || Lyrics
Nightcore Wolfie
My TOTALLY AWESOME Time in the World of Superbrothers: Sword & Sworcery EP
Grumpy Bear Gaymer
A Healthy Treat in Coron Palawan
Briscoe Travel
Шаффл Баттл Who BEST DANCER ? NEON MODE TUZELITY SHUFFLE
tuzelity SHUFFLE