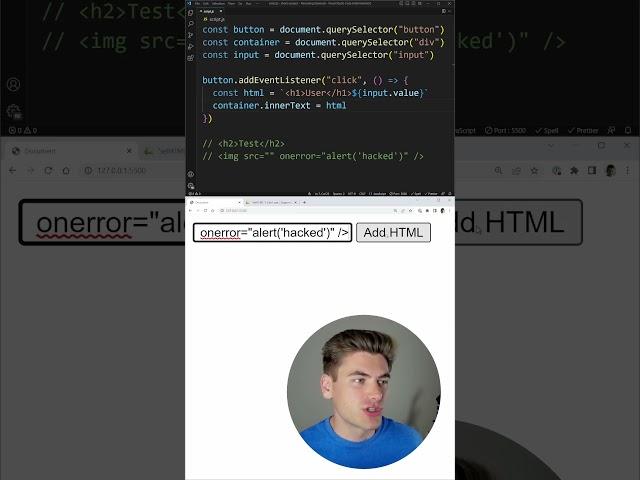
You Can Finally Safely Use innerHTML (kind of)
Комментарии:

Next video will be - NEVER USE setHTML
Ответить
What a great programmer man you helped me a lot in my projects, I have a video idea, you can talk about data URI like data:image/svg+xml or data:text/html or data:text/plain
Ответить
I feel disappointed because no one mention the 69.420% joke
Ответить
I think that is only useful if you fetch something from the server, not input directly, what is the point of sanitizing input which would you show directly without going through server, it’s the same thing as you messed thing up in developer tool, they can just do whatever they please with it
Ответить
how it is a "mistake" if it's not supported by most browsers
Ответить
.split('<').join('<')
Ответить
who cares tho... html is a joke
Ответить
not me forgetting that not everyone uses a framework, wow react really took over my workflow
Ответить
just a quick question, for javascript how can a user input hack a website? javascript is a client side code... so it doesn't matter ... anyone can use console to write any javascript code they want to run or test on any online page and run the code
Ответить
this video is total BS and makes me angry, clicking on the "Don't recommend channel button" cya
Ответить
Yea we needed this 20 years ago, that would have been real nice. So now we probably have 2 decades worth of applications out there vulnerable from developers that didn't know better back then.
Ответить
Can't I just use dev tools in my browser ?
Ответить
aren't we literally allowed to code in console? which is the same right?
Ответить
You are a hero!
Ответить
Microsoft having a feature that Firefox doesn't? Edge is much better than IE was.
Ответить
Idk what this guy is talking about… browser support looks “nice” to me 😊
Ответить
Chrome and disgusting edge ,
are corporate browsers that ,
nobody should develop around.
User can download another better private browser.
IDC. deal with it.
I am NEVER developing according to corporate standards.

So useless and even harmful if someone thinks that this would make the coder safer
Ответить
uh what? I can also go to the console and run javascript from there or modify the html...
Ответить
Anyone intelligent enough to inject custom HTML via form input would just use the dev console and inspector to inject whatever they wanted anywhere on the page so this is just silly and unnecessary. There is no such thing as client-side security—it's all just security through ignorance.
Ответить
No one use this 😂
Ответить
Umm... A malicious actor could accomplish the same from the console. This makes no sense as a tip.
Ответить
Tell me you went to a boot camp without telling me you went to a boot camp.
Ответить
Gonna start using this method from now on.
Ответить
but most of all, samy is my hero.
Ответить
A super common mistake developers make is that they think there is any security when their website runs on a browser on a computer that they don't own. The owner has access to and can modify every byte in that browser. They can add whatever java-script the want to your website, even without any inputs. Your website may even be running on a simulation of a browser.
Ответить
Ever opened the inspector in a browser and used the provided console there? xD
Ответить
Nice😁 but 70% is bad💀
Ответить
%69.42 💀💀💀
Ответить
Or, you know... You could use the escape function.... before you format a random string in.... I don't understand how you can be this stupid tbh. Why would you just use a format string with unescaped data?
Ответить
Cool
Ответить
browser support being 69.420% noice
Ответить
I can’t believe innerHTML became the standard for setting text in the DOM. Even recent tutorials still use it when it is way less secure than innerText.
Ответить
Or, you know, generate the DOM you actually want and insert it.
Ответить
I don't understand your point, if you want to add JavaScript in the client page, you Can just do it using thé browser console, or even rewrite the HTML of thé page.
Ответить
Yeah just did it to my to-do earlier.
Ответить
how about eval()
Ответить
If the client machine wants to break itself with some malicious JS I don’t care, won’t get past my server validation 😂
Ответить
Great, but this is still in the front end 😢
Ответить
there are so many other way to clean your input, why giving people bad advice?
Ответить
Super common mistake that developers make is using JavaScript
Ответить
🎉 thanks for this
Ответить
I have never understood why people do it like this. Create the element instead and insert user supplied text with textContent instead.
Ответить
The percentage is literally 69.420%...
Ответить
really thanks
Ответить
Doesn’t like SVG either. Instead I'm using a custom named template literal function that returns a DocumentFragment to append.
Ответить
ChatGPT said this video is wrong, in the sense that you can just use sethtml instead of innerhtml. it says it only works in some very specific areas.
Ответить
documentation says that sethtml is still experimental and still not supported
Ответить
Hm caniuse doesn’t seem to show this anymore. I can only find setHTMLUnsafe which (if I’m reading MDN correctly) DOESNT sanitize. Gah what happened to this method ?!
Ответить