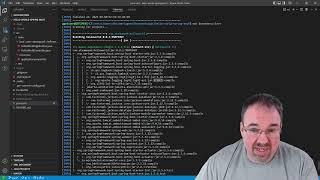
Finding and Remediating Vulnerabilities with Maven Dependency Management
Комментарии:

Thank you for such detail video on solving vulnerabilities in Java applications. "
Before bumping the versions of jackson-databing and logback-core in <dependencymanagement> section, we could see these dependencies were coming from some other sources. When we want to bump these versions, don't we exclude these dependencies from their earlier sources?

ThanX! This is very useful and I gave it a like, but... don't you think we would like to see commands you are typing rather than the content that covers them?
Could you put them in description?

This is the best video on the subject that is out there. VIdeo is missing some important tactics:
1. Using Maven enforcer
2. Using mvn dependency:tree -Dverbose with -Dincludes option

in this video you can find that why we should use dependency management tag especilly i got
Ответить
Love the way a simple Sprint app takes ages to compile
Ответить
Thank you, sir. You are a life saver.
Ответить
Thank you for sharing! Sometimes top level dependencies are downloading their transitive dependencies even if they are not used in your project. I wonder, is there any easy way to check if a transitive dependency is used for the project?
Ответить
Still the tricky thing to find is with the plugins. maven-complier-plugin downloads many old plexus-utils jars which come under critical vulnerabilites. How to fix those such that the plugin takes latest of plexus-utils
Ответить
Hi, how to resolve CVE-2016-1000027?
Ответить