How Hackers Steal Your Browsing Data | Your Web Browsing is Secure?
Discover the hidden dangers lurking online in our latest video, These Ways Hackers Steal Your Browsing Data"! Dive deep as we unveil the tactics hackers use to exploit your browsing habits—from phishing attacks to session hijacking. Learn how these cybercriminals operate through fake emails, malicious browser extensions, and unprotected public Wi-Fi networks. We’ll also share essential tips on how to protect yourself, including the importance of strong passwords, using a VPN, and keeping your software updated. Don't fall victim to these threats! Like and share this video to spread awareness.
#CyberSecurity #Phishing #DataProtection #OnlineSafety #Hackers #Malware #VPN #Privacy
Phishing Attacks
Browser Extensions
Man-in-the-Middle (MitM) Attacks
Malware Installation
Exploitation of Browser Vulnerabilities
Session Hijacking
Public or Shared Devices
DNS Hijacking
How to Protect Yourself
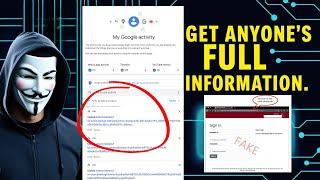
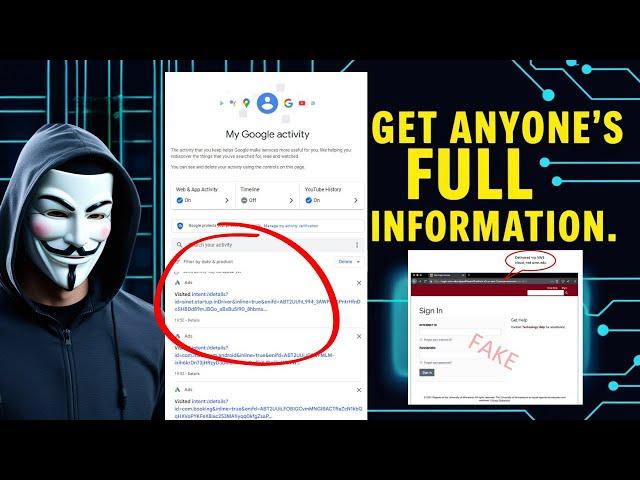
Your Browsing History
Data Recovery Techniques
A False Sense of Safety?
Operating System Logs
Hardware-Level Recovery
Social Engineering and Phishing
Malware Infections and Network Monitoring
ISP Data Retention Policies
Safe Browsing and Cybersecurity
✦ Disclaimer ✦
These videos are for educational purposes. All images and video footage used is credited within the video but copyright remains with the original owners. Copyright Disclaimer under section 107 of the Copyright Act of 1976, allowance is made for “fair use” for purposes such as criticism, comment, news reporting, teaching, scholarship, education and research. Fair use is a use permitted by copyright statute that might otherwise be infringing.
*For Promotion & Collaboration Contact me*
👇🏻👇🏻👇🏻👇🏻
📧 Gmail: [email protected]
Follow me on my social media accounts for any queries
📱 Instagram: https://www.instagram.com/cyberhouseyt
🐦 Twitter: /https://x.com/cyberhouseyt
🔺 Youtube: https://www.youtube.com/@cyberhouseyt
🌐 Website: https://cyberhouseyt.blogspot.com/
-------------------------------------| Thanks |--------------------------
#CyberSecurity #Phishing #DataProtection #OnlineSafety #Hackers #Malware #VPN #Privacy
Phishing Attacks
Browser Extensions
Man-in-the-Middle (MitM) Attacks
Malware Installation
Exploitation of Browser Vulnerabilities
Session Hijacking
Public or Shared Devices
DNS Hijacking
How to Protect Yourself
Your Browsing History
Data Recovery Techniques
A False Sense of Safety?
Operating System Logs
Hardware-Level Recovery
Social Engineering and Phishing
Malware Infections and Network Monitoring
ISP Data Retention Policies
Safe Browsing and Cybersecurity
✦ Disclaimer ✦
These videos are for educational purposes. All images and video footage used is credited within the video but copyright remains with the original owners. Copyright Disclaimer under section 107 of the Copyright Act of 1976, allowance is made for “fair use” for purposes such as criticism, comment, news reporting, teaching, scholarship, education and research. Fair use is a use permitted by copyright statute that might otherwise be infringing.
*For Promotion & Collaboration Contact me*
👇🏻👇🏻👇🏻👇🏻
📧 Gmail: [email protected]
Follow me on my social media accounts for any queries
📱 Instagram: https://www.instagram.com/cyberhouseyt
🐦 Twitter: /https://x.com/cyberhouseyt
🔺 Youtube: https://www.youtube.com/@cyberhouseyt
🌐 Website: https://cyberhouseyt.blogspot.com/
-------------------------------------| Thanks |--------------------------
Тэги:
#cyber_house_yt #hacker #hacking #cracker #cracking #kali_linux #kali #metasploit #ethical_hacking #ethical_hacker #penetration_testing #penetration_tester #owasp #Man-in-the-Middle #Hijacking #Phishing_Attacks #Browser_ExtensionsКомментарии:
How Do I Change My Country on Twitter (X)
a2zhow (A to Z How) - Website Guide
Бехруз муминов очаи хору зорм
Madina Davlatova Official
拜年-Ken Choh 曹今铭,陈美娥,潘秀燕 ,薛鸣
StarSea168
Распаковка антиМоскитного кокона #зубарев #китай #отец
Zubarefff team